There is RFID market potential in every product that can be counted, inventoried, or sold. Although inventory and point-of-sale activities will comprise the lion’s share of the RFID tag market, applications that go a step beyond identification are growing faster. Retail products that are tagged enable not only inventory control but dynamic changes in pricing. Library books, pharmaceuticals, livestock, and airport luggage are tracked with RFID. Hospitals use them to keep track of patients, staff, medications, and equipment. Access control enabled by keyless entry using RFID-enabled fobs and smart cards are already in use. However, now RFID is also being combined with biometrics in applications such as ePassports and health records. The market for RFID tags is expected to accelerate. IDTechEx, for example, forecasts that 250 billion tags will be sold in 2021 – up almost ten times from the three billion units sold in 2011.
Although NFC is part of the RFID technology spectrum, its unique capabilities set it apart. Strong security starts with NFC’s less than 10 cm operating distance, and can be enhanced with SIM chips and cryptography. NFC was designed to be easy-to-use and to simplify other technologies as well. The widespread adoption of NFC into mobile phones that began in 2011 has opened the door to many new applications. Manual pairing is becoming a thing of the past. NFC can act as a bridge between a Wi-Fi router and any other computer peripheral or device by effortlessly passing set-up information from the device to the router. According to IMS Research, NFC applications are growing rapidly. The number of NFC-enabled mobile phones will grow ten times between 2012 and 2017, reaching 1.2 billion units, as manufacturers adopt wireless communications and payment technology in their products as a de facto standard.
RFID
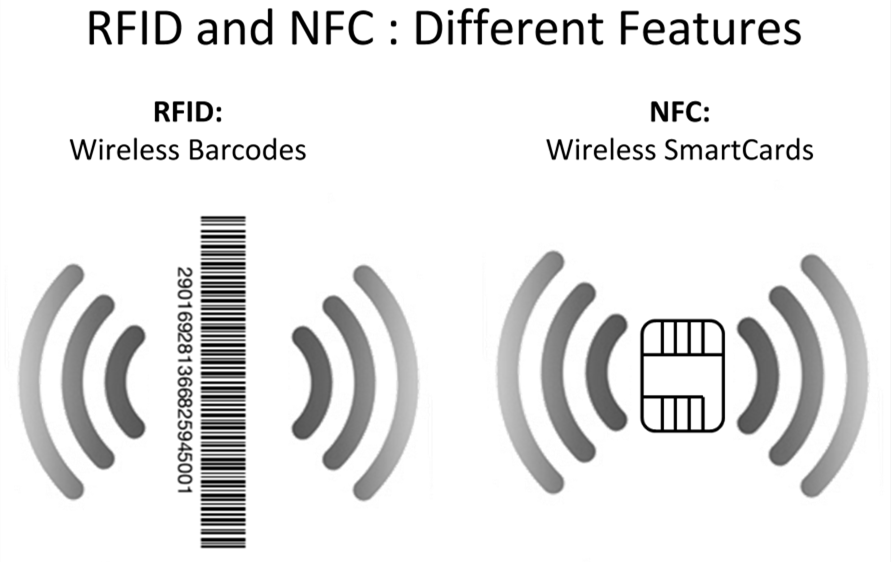
RFID NFC difference in the technologies is very complex. It has many implementations that vary according to frequency, protocol, and antenna design. But most RFID variants have two things in common: (1) Communication is bi-directional and takes place between a very inexpensive RFID tag and a considerably more sophisticated RFID reader; and (2) the information exchanged tends to be 2 Kbits or less – usually much less. In the vast majority of cases, the tag has no power supply – it harvests energy from the reader to transmit its identification information. In most cases, energy is transferred though inductive coupling, which could be thought of as a transformer with an air core created by the distance between the tag and the reader. Reading range is determined by carrier frequency and the power generated by the reader. RFID systems that operate at UHF frequencies can achieve a considerable greater reading range through a phenomenon called backscatter coupling and in some instances by providing an energy source to the tag.
The design challenges posed by RFID systems are considerable, but RFID NFC difference from those of high-performance computing and communications designs. Performance is often measured by the number of tags that can be read simultaneously, reading accuracy, and ease-of-use. RFID design challenges also arise from considerations such as system cost, reading range, the multiplicity of protocols that could be used, antenna design, and the system’s operating environment: wet, dirty, dusty, hot, noisy, etc. By far the most difficult challenges would be posed by the application itself, which may be as simple as the exchange of a few hundred bits of identification information, or as demanding as keyless access that requires authentication. Other high-end applications include point-of-sale activities, pharmaceutical tracking that is subject to regulatory oversight, ePassports, and factory automation in which a tag can activate a programmable logic controller.
Although RFID systems can use many carrier frequencies, three dominate the market: LF, which uses the 125 to 135 KHz band; HF, which operates at 13.56 MHz; and UHF, which primarily is used in the 865 to 955 MHz band. The 2.4 GHz band may also be included in UHF. Semiconductor companies design the transponders that are embedded in the tags. Inlay manufacturers (including IC companies) integrate the transponder into a tag that typically includes little more than the transponder, memory, and an antenna, of which there are many designs.
NFC
NFC (Near Field Communications) is becoming ubiquitous as a means of transferring information securely between a growing number of electronic devices and with an absolute minimum of effort. Virtually any product with an MCU or CPU can become more useful and user friendly when it is NFC-enabled. NFC is a subset of RFID: It operates in the RFID HF (13.56 MHz) carrier signal range; is interoperable with legacy smart-card protocols; and delivers far more value than information exchange.
When the first NFC standard was developed about ten years ago, ease-of-use was just as important as security. At the time, pairing Bluetooth devices was a challenge to many users, as was setting up Wi-Fi networks by keying in several network authentication parameters. A key NFC achievement is that it provides an effortless solution. Its short read-range and automatic authentication allow end-users to transfer network and pairing parameters from one NFC device to another. Simply tapping” the first device with, for example, an NFC-enabled mobile phone and then tapping the other device with the phone is all it takes.
Another dimension of NFC’s ease-of-use is the support for legacy RFID protocols. Two NFC devices communicate with each other over a specific protocol, but NFC-enabled devices can also operate with all popular smartcard protocols as well. The rapid introduction of NFC into mobile phones enables NFC’s penetration into the important point-of-sale (POS) market. An NFC-enabled phone can also read passive RFID tags embedded in advertisements or maps and use this information to access a website for more information.
From an engineering perspective, NFC has three operating modes: Card emulation mode, in which NFC device behaves like an existing contactless card; reader/writer mode, in which the NFC device reads or writes to a passive legacy RFID tag; and peer-to-peer mode in which two NFC devices exchange information.